In this article, we demonstrate how to protect and secure services located behind a Kemp LoadMaster load balancer or proxy by integrating it with Keycloak. This integration enables Single Sign-On (SSO) and Identity and Access Management (IAM) for your applications, while keeping selected public services accessible without authentication.
1. Preparing the Configuration in Keycloak
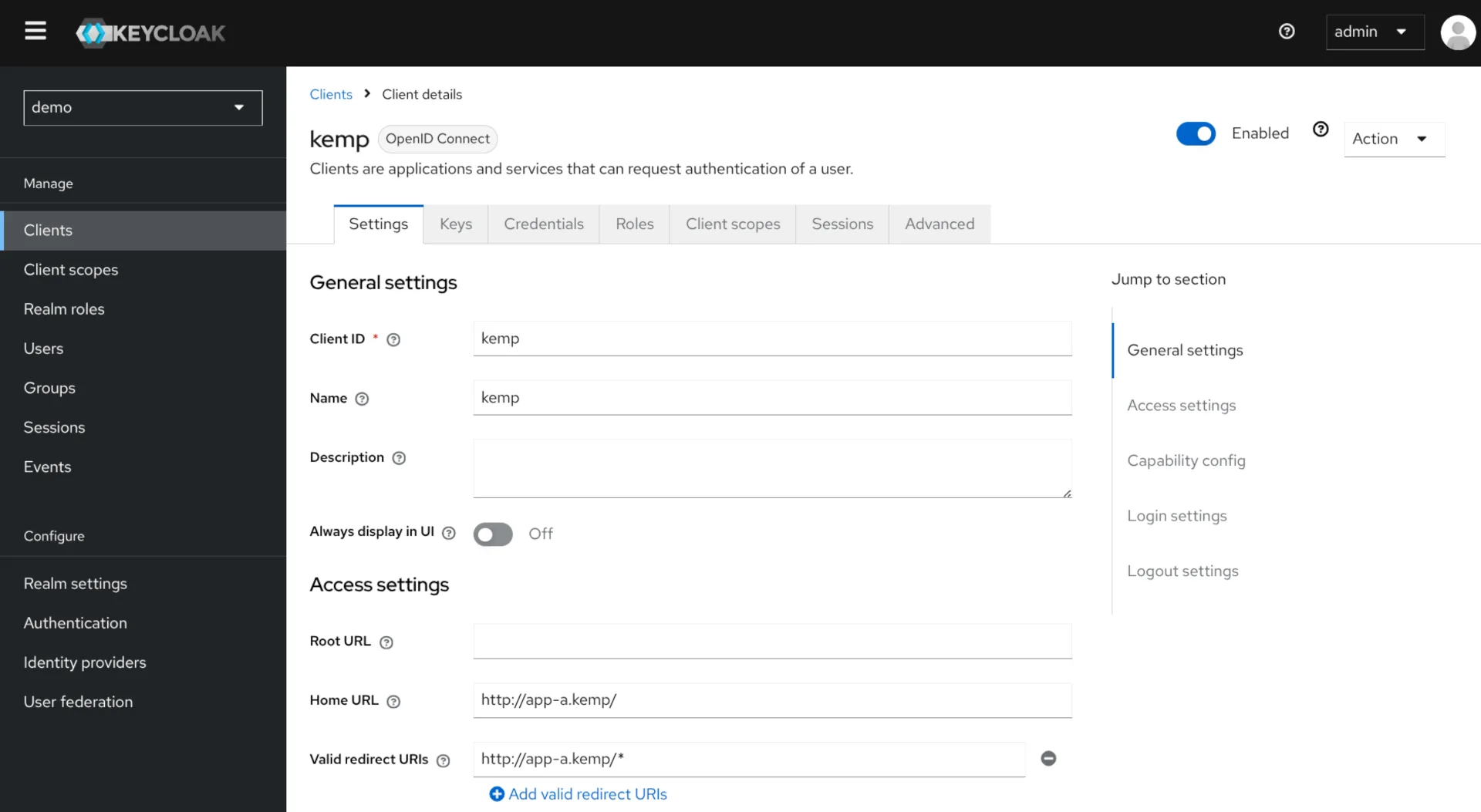
The first step is to configure the client in Keycloak for the service you want to secure. This client represents the target application or service (e.g., app-a.kemp) and must be correctly set up in the Keycloak realm with all required authentication and authorization parameters.
2. Setting Up the SSO Domain in Kemp LoadMaster
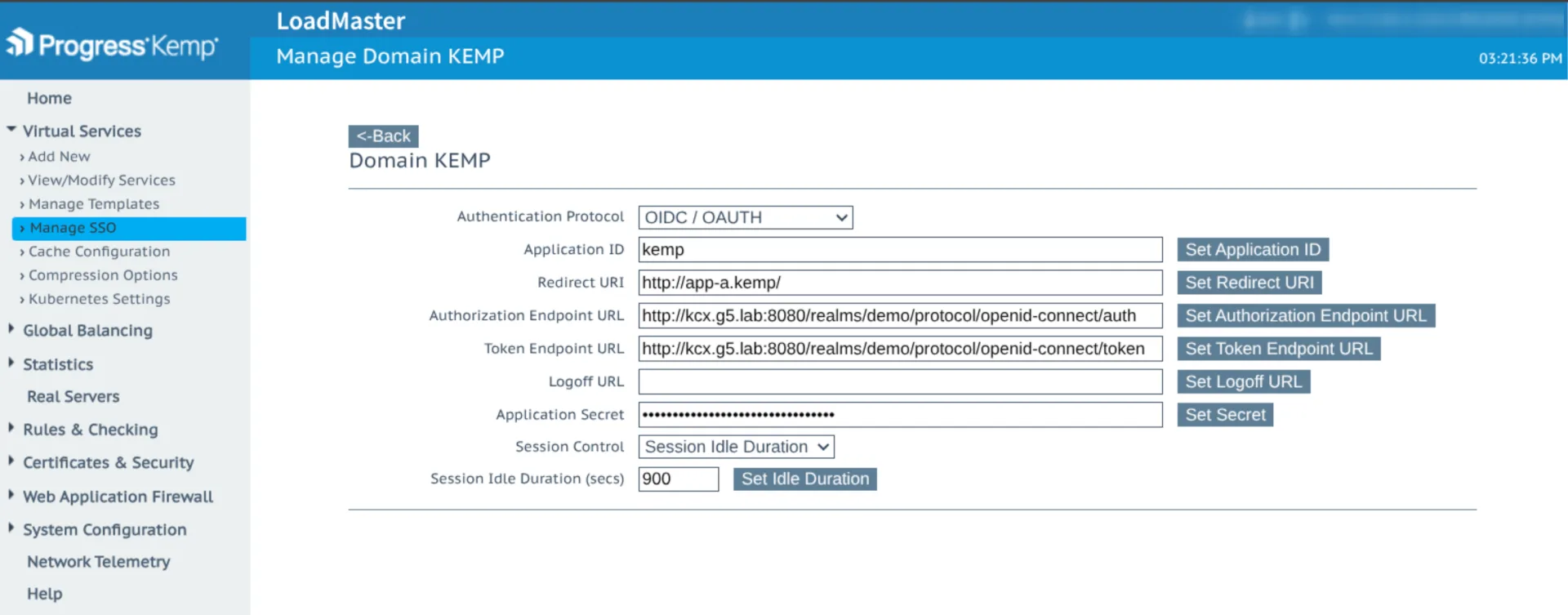
On the Kemp LoadMaster side, we create an SSO Domain (called KEMP in our example) and configure the following:
Token endpoint
Authorization endpoint
The target service to be protected (e.g., app-a.kemp)
This SSO Domain allows Kemp to interact with Keycloak for user authentication.
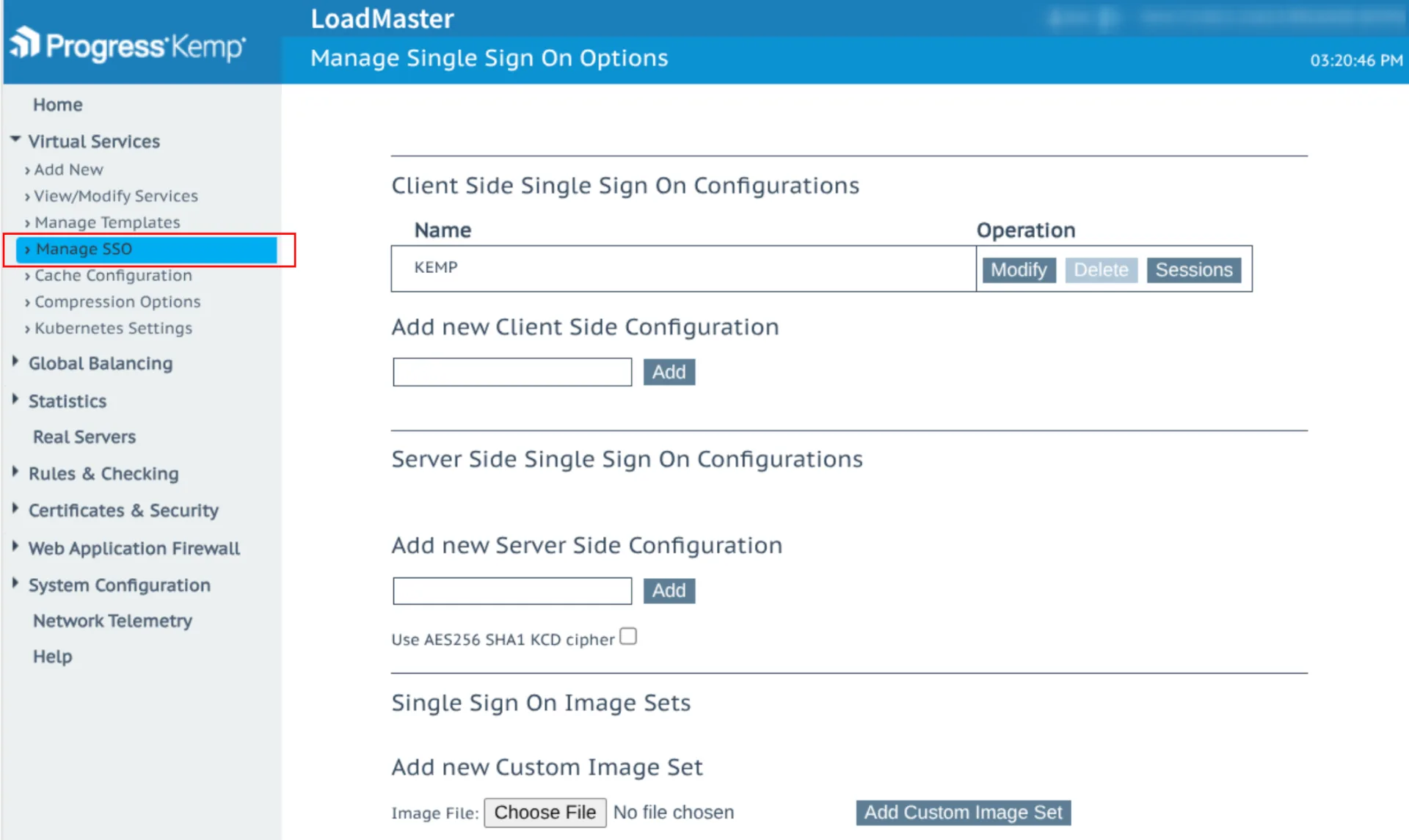
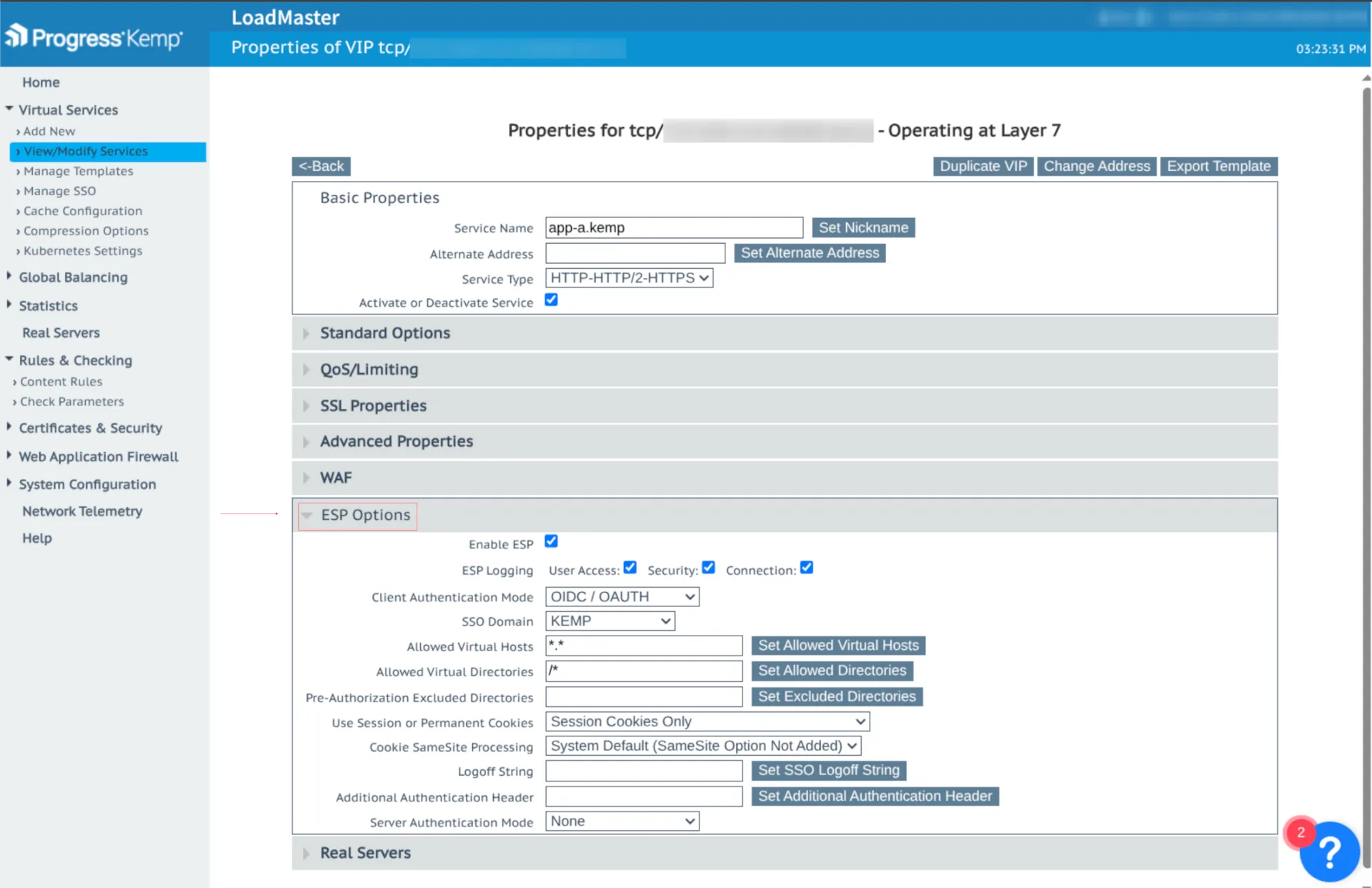
3. Enabling ESP (Edge Security Pack)
To enforce security for the service, we link the SSO Domain to the Virtual IP (VIP) corresponding to the application we want to protect. This is done by enabling the ESP option in the VIP settings.
For services you want to leave publicly accessible, simply do not enable ESP.
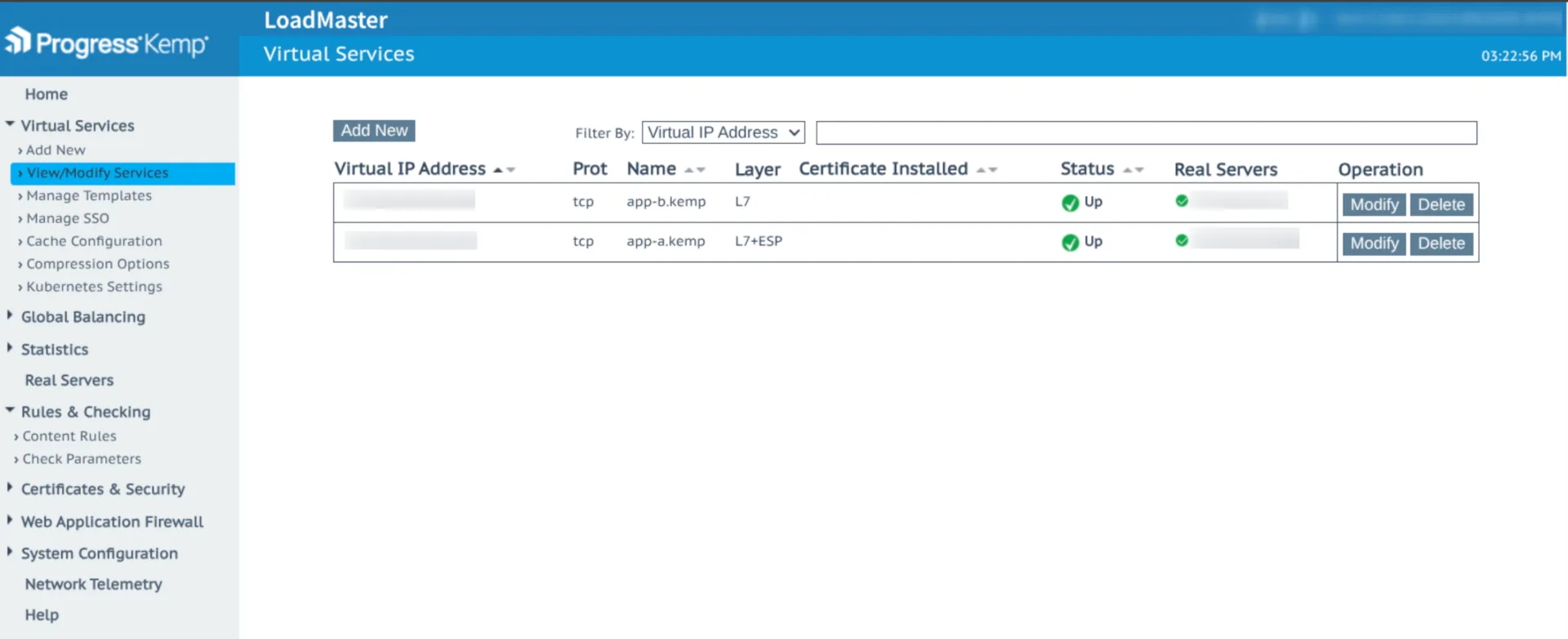
4. Testing the Keycloak / Kemp LoadMaster Integration
Case 1 – Unprotected Service
Application: app-b.kemp
Expected result: direct access without authentication.
Test: immediate access, no Keycloak redirection → ✅ works as expected.
Case 2 – Protected Service
Application: app-a.kemp
Expected result: redirect to the Keycloak login page before access.
Test: redirection happens, user logs in, service becomes accessible after authentication → ✅ integration successful.
Conclusion
This demonstration confirms that it is entirely possible to secure services behind Kemp LoadMaster through a Keycloak integration.
With this approach, you can implement:
Centralized Single Sign-On
Multi-Factor Authentication (MFA)
Granular access control
Unified user and role management
Looking for Keycloak Experts?
If you’re planning to integrate Keycloak into your IT infrastructure, we can assist you from design to production deployment.
📩 Contact us today to discuss your project and secure your services.



